Zero Trust Model: Redefining Cybersecurity in the Modern Digital Age
The Zero Trust security model is a cloud-based, comprehensive approach to cybersecurity that challenges the traditional perimeter-based security mindset.
It revolves around the principle of not trusting anyone or anything by default, regardless of their location within or outside the network perimeter. This model promotes continuous verification and validation of user identities and devices and requires strict access controls and authentication, whether inside or outside the network.
As we continuously navigate the complexity of the modern work environment, especially businesses that embrace hybrid workplaces, you can never have too much security to adequately protect an organization’s people, devices, and data. Zero trust adds that extra layer of security that businesses desire while also addressing the need to combat cybercrime which is currently predicted to cost businesses around the world a staggering $9.5 trillion in 2024 according to the statistics presented in the 2023 Official Cybercrime Report by Cybersecurity Ventures.
The Core Principles of Zero Trust
“Never trust, always verify” sums up exactly what the zero trust security model does. To further understand what exactly zero trust is, let us cover the core principles of this no-nonsense cybersecurity method.
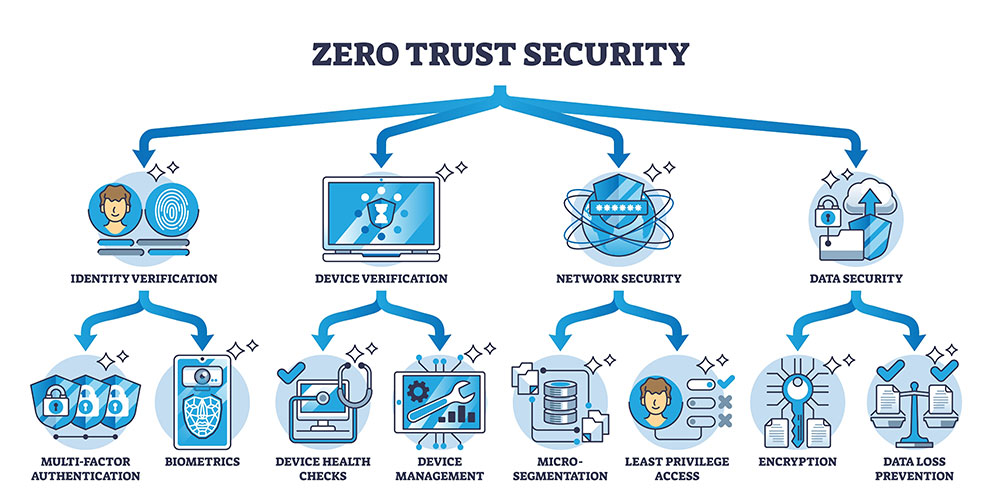
- An Inline Approach – This considers all traffic potentially hostile, and it is blocked until validated by the previously determined attributes.
- Micro-segmentation – A practice that divides security perimeters into smaller zones to maintain separate access to different network components. This separation means that a user or a device with access to one zone will not be able to access others without prior separate approval.
- Explicit verification – A practice that authenticates and authorizes every user and device on every session.
- Multi-factor authentication – A practice that coincides with explicit verification, MFA is when more than one piece of identification is required to authenticate a user. This can be a password in addition to a passcode on their phone, security questions, or something physical like a thumbprint or security badge.

- Principle of least privilege – This strategy grants individuals’ access to the resources they are using for only as long as they need them, in other words, they receive the bare minimum levels of access that are necessary to effectively perform their roles. This strategy is efficient for reducing the potential of insider threats and limited access reduces the risk of data breaches.
- Assume a Breach – This mindset means acting as though your network has already been breached or a breach will inevitably happen. While this seems extreme, this proactive approach emphasizes damage limitation by implementing protective measures such as limiting access to resources, end-to-end encryption, and the use of analytics to monitor network activity and detect potential threats. This mindset is not only great for preparing for potential threats but prompting organizations to stay alert.
Best Practices for Better Results
Zero trust has earned its place as one of the most effective means of ensuring cloud security for businesses. It can be applied across your entire IT ecosystem including your applications, data, endpoints, identities, infrastructure, and network. This deeply intertwined security method that inherently trusts no connections without proper verification can reduce the attack surface and overall risk of a data breach, have increased visibility into network traffic, limit the blast radius of breaches, support compliance initiatives, and have constant, adaptable security.
When designing a zero-trust architect there are questions to keep in mind before implementation:
- Does this protect the data and assets that need protection?
- From whom is a business trying to protect these assets and does the strategy address this?
- Does the basics of your zero trust network do the following: Log and inspect all corporate network traffic, Limit and control access to the network, Verifies and secures the network and resources
Ideally, your zero-trust architecture should be done with help from IT professionals who understand your IT environment so that critical data, assets, applications, and services (DAAS) can be easily identified. To further make this strategy work, as preparation and best practices businesses should:
- Map transaction flows to understand how data moves within the business
- Make an organization-wide commitment
- Identify all IT and data assets and assign access rights based on roles
- Lockdown vulnerabilities early
- Classify data for a data-centric approach
- Segment networks to prevent lateral movement
- Isolate and protect workloads
- Regularly monitor and log activities to ensure compliance with Zero Trust
- Deploy security measures that adapt to change landscapes like automated systems that can detect and respond to anomalies and regular updates of security protocols
It is Time for Zero Trust
Zero trust is not an overnight fix but a cybersecurity overhaul for a business, so it can be intimidating to make the jump. Understanding what your business needs is the first step in deciding on zero trust but there are plenty of signs that point to zero trust being right for an organization. These can include businesses that have a multi-cloud, hybrid of multi-identify infrastructure, unmanaged devices, legacy systems, and software as a service (SaaS) apps. Another sign zero trust might be right is if the organization needs to address key threats such as ransomware, supply chain attacks, and insider threats, especially if they are frequent.
Zero trust models are also ideal for organizations that share resources or collaborate with third parties including vendors, partners, or customers since access to resources can be granted on a per-request basis. This also helps when dealing with data centers, since they often contain a large number of servers and devices connected to the same network. With micro-segmentation businesses have the ability to keep access to resources in segmented, controlled areas meaning cyber attacks can be limited and attackers will have difficulty moving laterally within the center.
Facing the Reality
Whether businesses like it or not, cybercrime and attacks are quickly becoming more efficient, and basic security is not enough in the modern, more hybrid working Era. Layers of cybersecurity are recommended for top protection and having strategies as powerful and efficient as zero trust within those layers helps ensure businesses that their data, employees, customers, bottom line, and all other valued aspects are out of reach of cyber attackers.
If you have questions about the zero trust model, how to implement it, cyber security, or IT services in general contact us at AIS today!


